- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
This is an early preview of what the Portfall project has coming soon.
@Lipaydi and I ( @Asphyxia ) are working jointly to speedily develop open source security tools in the PHP language.
Due to simplicity I will be deploying and developing this via Ubuntu for beta, when we are ready - we will have a CentOS release for stable.
Toss this within portfall.php and save:
Now you should be able to load portfall.php and you will notice when you click 'Scan', results will begin showing in real-time.
If a large enough scan is executed, you may need to adjust the phpseclib timeout via:
Caution: You are responsible for launching port scans. Please be responsible!
Screenshot
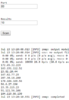
---
For an example of what you can do with Nmap:
Paste this inside nmap.php for scanning yourself:
Keep in mind you may change "nmap localhost" to "nmap 192.168.1.*" for example, to scan your local network. For the purpose of parsing, you may want to write the scans out to a file like:
Also, Nmap has built-in scripts within /usr/share/nmap/scripts/.
An example of fetching help for the plugins is shown above.
... more coming soon.
@Lipaydi and I ( @Asphyxia ) are working jointly to speedily develop open source security tools in the PHP language.
Due to simplicity I will be deploying and developing this via Ubuntu for beta, when we are ready - we will have a CentOS release for stable.
Bash:
apt update
apt upgrade -y
apt install apache2 php unzip zmap -y
cd /var/www/html
wget https://github.com/Sovietgate/R4P3/raw/master/phpseclib1.0.16.zip
unzip phpseclib1.0.16.zip
nano portfall.phpToss this within portfall.php and save:
PHP:
<pre>
<form action="portfall.php" method="GET">
<p>Port<br><input type="text" name="port"></p>
<p>Results<br><input type="text" name="resultMax"></p>
<input type="submit" value="Scan">
</form>
<hr>
<?php
if(isset($_GET['port']) && isset($_GET['resultMax']))
{
$port = intval($_GET['port']);
$resultMax = intval($_GET['resultMax']);
include('Net/SSH2.php');
$ssh = new Net_SSH2('localhost');
if (!$ssh->login('root', 'N4n@32x7X+')) {
exit('Login Failed');
}
function packet_handler($str)
{
echo $str;
flush();
ob_flush();
}
$ssh->exec('zmap -p '.$port.' -N '.$resultMax, 'packet_handler');
}
?>
</pre>Now you should be able to load portfall.php and you will notice when you click 'Scan', results will begin showing in real-time.
If a large enough scan is executed, you may need to adjust the phpseclib timeout via:
Code:
$ssh->setTimeout(0); //should disable timeout
$ssh->setTimeout(100); //should timeout in 100 secondsCaution: You are responsible for launching port scans. Please be responsible!
Screenshot

---
For an example of what you can do with Nmap:
Code:
apt install nmap -y
nano nmap.phpPaste this inside nmap.php for scanning yourself:
PHP:
<pre>
<?php
include('Net/SSH2.php');
$ssh = new Net_SSH2('localhost');
if (!$ssh->login('root', 'N4n@32x7X+QFa1XS')) {
exit('Login Failed');
}
function packet_handler($str)
{
echo $str;
flush();
ob_flush();
}
$ssh->exec('nmap localhost -v', 'packet_handler');
?>
</pre>Keep in mind you may change "nmap localhost" to "nmap 192.168.1.*" for example, to scan your local network. For the purpose of parsing, you may want to write the scans out to a file like:
-oX test.xml :: writes in XML format
-oN test.txt :: writes out a text file
-oG test.txt :: greppable as results are written out by line
Also, Nmap has built-in scripts within /usr/share/nmap/scripts/.
Code:
<pre>
<?php
include('Net/SSH2.php');
$ssh = new Net_SSH2('localhost');
if (!$ssh->login('root', 'N4n@32x7X+QFa1XS')) {
exit('Login Failed');
}
echo $ssh->exec('ls /usr/share/nmap/scripts/');
echo "<hr>";
echo $ssh->exec('nmap --script-help teamspeak2-version.nse');
?>
</pre>An example of fetching help for the plugins is shown above.
... more coming soon.
Last edited: