You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Web security development team
- Thread starter Asphyxia
- Start date
- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
- Thread starter
- #6
We are going to start making a basic port 80 and 443 scanner in C++:
Download and install Simple and Fast Multimedia Library matching your C++ environment: https://www.sfml-dev.org/download/sfml/2.5.1/ the latest version right now is 2.5.1 but this is SUBJECT TO CHANGE in the future so use this link for the latest version.
I am assuming most people use Windows but well fuck that. My advice? Switch to any *nix shit, any OS that feels UNIXY.. if you are afraid then use Ubuntu https://ubuntu.com/download/desktop or if you really enjoy Windows because you like gaming, then run Windows as your host OS (keep your Windows patched regularly though - think BlueKeep and EternalBlue).
Run something like VirtualBox (FREE) or VMware ($$$), put any Linux inside there for example Debian or Ubuntu.
I like to type apt instead of yum, so if you use something like CentOS you will be typing shit like "yum install httpd" instead of "apt install apache2" - package names are different and.. you know, different package managers, different names, and shit. So make your life easy and use something like Debian or Ubuntu - be a real man.
Even if you install apt package manager on CentOS, RHEL-family shit uses yum dominantly so you could "yum install apt" but then you might be missing packages. RepoForge (formerly RPMForge) used to often manage RPM packages for: Red Hat Enterprise Linux (RHEL), CentOS, Scientific Linux
Nowadays "RPMForge/!RepoForge - This is a dead project. Not maintained. DO NOT USE.".. this brings me to another topic on converting RPM to DEB packages. Anyway, your life in the Linux or overall *nix world is going to change. You will be like "wtf, I just spent 6 hours trying to install an image editor" and.. that is why Linux is so fucking fun! Because you have to figure shit out. On Windows sure you can click install and life goes on, but you never realize what went into making that happen - probably.
Start learning today, switch to Linux or at least begin running any Linux distribution in VirtualBox or VMware. What are you waiting for in 2020? Fucking do it! Be an Internet ninja with me... us.
Forget MSI and say hello to RPM and DEB - https://unix.stackexchange.com/a/374229 .. sure you type more commands and shit, but once you learn how these commands work, what they do, your life will change for the better - things get done faster and you might see file sizes like 2MB instead of 18MB. Because Linux is beautiful.. and Windows is bloated, full of extra, and in my opinion sometimes and actually most of the time you will find better stability within the Linux world.
With that said, get Debian or Ubuntu inside VirtualBox or VMware.
Now.. let me say that you can just use an ISO file to install your own VM. I actually recommend this most for security reasons. With the osboxes virtual image, you are trusting some random fucker - jk but not really jk.. some person on the Internet installed the iso inside VirtualBox or VMware then took the VM file - then they upped it to SourceForge so you are going from trusting the Debian ISO, to trusting the Debian ISO, the ISO installer man, and trusting SourceForge.. additional risk of 2 parties. Fuck that! Give me the original source - every time.
Debian ISO: https://www.debian.org/distrib/netinst - click amd64 as amd64 = AMD and Intel 64-bit processors we will see 32-bit architecture losing support as we get closer to 2030s but even now 32-bit just sucks ass - so anytime you see "amd64" get excited and do that - every time. If you don't need amd64 then you probably know what you need, I hope!
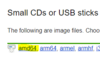
Ubuntu ISO: https://ubuntu.com/download/server

Then you will take your ISO file of Debian/Ubuntu and load into your VM (virtual machine). Keep in mind that your hypervisor of choice is great at providing virtualization.. but will only take the resources you provide it. You'll want to give your virtual environment plentiful RAM and CPU to work with. I typically go half-half for example if I have 16GB of RAM, I'll give my virtual environment 8GB RAM.
Now let's move onto actually using our VM to begin making a website scanner (firstly we will check port 80 and 443) as these are the most common website ports - HTTP (80) and HTTPS (443). Port 80 is used for unencrypted website traffic, so if you login to a website using http:// and not https:// your password "Horse1" gets sent across the whole fucking hops nodes path as "Horse1" instead of scrambled w/ encryption like "fiaef89wef89w0rt4965654y89t98g98g8959y5"*bits cryption... so yeah, umm HTTPS is pretty fuckin' good - real talk. Port 443 is better than port 80 for security, because encryption keeps information safer while in transit. It's like bulletproof armor walking through a war zone. Turn HTTPS (443) on and let HTTP (80) die. Can you still get sniped in the head with a sniper rifle? Sure, but you are protecting your heart (password) and other vital organs (username and involved systems) from stray bullets like basic MITM/sniffing of traffic.
This brings me to one other point, downloading files over HTTPS (443) is far safer because otherwise it is a possibility someone could more easily provide you an incorrect file. Let's say you go to download an ".exe" file, an attacker on WiFi could perhaps feed you a malicious executable file you then launch on Windows. Wouldn't you see other stuff look wrong though? Someone could proxy the requests through and when you fetch the exe, only then they offer the malicious binary. It may sound complicated and overly complex, but this shit is easy. They pretty much make run-click-fuck attacks nowadays. So use HTTPS.
It's more common to have prepackaged tools for causing damage than in past years, because as security is improving, attacks are being made easier to launch because attacks are getting stronger with ease-of-use in mind. It's a back-and-forth battle between security and anti-security. Many describe this as "cat and mouse".
'ways, here we are.

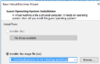
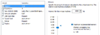
RAM: 4096
CPU: NUM of proc = 2, NUM of cores = 2
All set: Close, Finish
Power on this virtual machine
---
The instructions for VirtualBox are different, I used VMware so figure VirtualBox yourself or find a VMware key online lol (like maybe the store if you have money or whatever..).
If you are new, continue on using Graphical install. This walks you through installing the Linux system. Mostly just click Continue/Next through.
A point will be reached, you will see "Hostname:" set this to dev.ciphers.pw
If you want...
For the root password set something safe like: Bad#Guess2day
Name for new user: Ciphers
Username: ciphers
Password: Bad#Guess2day
Same user pass as root pass ftw, super secure!
For the disk partitioning:
Guided - use entire disk
Keep clicking Continue/Next until you get to...
Partition disks... "If you continue, the changes..."
SELECT "Yes", Continue
Your Debian system will install...
With the above password, I am certainly assuming you are not setting this up to be Internet accessible via SSH.
In the case you are being a dumb clown (unintentionally) and I have to make this tutorial dumb enough for those newly people, I will do that a little below.
"If you wish to scan another CD"... No, Continue
Keep clicking Continue/Next through the remainder.
When prompted for "popularity-contest", leave No selected and Continue.
Uncheck everything except "Debian desktop environment" and "standard system utilities".
When asked to install the GRUB boot loader, keep Yes and Continue.
Select /dev/sda ... Continue.
You will now be installing the system and almost ready to begin actually making your (probably first ever) port scanner on a Linux system - in C++.
---
We will be using GCC, keep in mind MinGW is a port of GCC over to the Windows OS... anyone wanting to make this on Windows can but I promise making this on Linux is going to be more exciting.
Login to your freshly installed Linux system with your password (or Bad#Guess2day).
Top right click Activities > search Term > Enter
This opens Terminal.
When prompted "Password:", enter your password (or Bad#Guess2day).
On Linux, the text password characters will not appear as you type. This is intended for obvious security reasons, similar to * showing up in a password field.
GCC is good
We should also get g++
Type "Y" for yes, Enter, to install gcc.
Alternatively you may install this as mentioned in the SFML tutorial.
We will be referencing two pieces, firstly this https://www.sfml-dev.org/tutorials/2.5/network-socket.php and secondly this old dinosaur of a scanner code http://www.cplusplus.com/articles/o2N36Up4/
Do this
... okay tbh fuck idk man - just fuck.
Let's just make a text file (CPP) in our home folder:
Save this to your file (Ctrl+X), Y, Enter
You will probably have an "a.out" file appear.
Now... install a web server and launch it to start port 80 listening.
Run your compiled single port checker
Shutdown your Apache web server:
We will now see if we run our port 80 checker tool:
We see:
This is not super complex or crazy awesome - but this is a VERY basic port scanner at that and you have just been shown how to compile this to be working.
From here, you have the basics to get started with a larger project that can go on to scan more ports, maybe optimize the code and read a hosts list etc.. hope this was fun and simple.
Download and install Simple and Fast Multimedia Library matching your C++ environment: https://www.sfml-dev.org/download/sfml/2.5.1/ the latest version right now is 2.5.1 but this is SUBJECT TO CHANGE in the future so use this link for the latest version.
I am assuming most people use Windows but well fuck that. My advice? Switch to any *nix shit, any OS that feels UNIXY.. if you are afraid then use Ubuntu https://ubuntu.com/download/desktop or if you really enjoy Windows because you like gaming, then run Windows as your host OS (keep your Windows patched regularly though - think BlueKeep and EternalBlue).
Run something like VirtualBox (FREE) or VMware ($$$), put any Linux inside there for example Debian or Ubuntu.
I like to type apt instead of yum, so if you use something like CentOS you will be typing shit like "yum install httpd" instead of "apt install apache2" - package names are different and.. you know, different package managers, different names, and shit. So make your life easy and use something like Debian or Ubuntu - be a real man.
Even if you install apt package manager on CentOS, RHEL-family shit uses yum dominantly so you could "yum install apt" but then you might be missing packages. RepoForge (formerly RPMForge) used to often manage RPM packages for: Red Hat Enterprise Linux (RHEL), CentOS, Scientific Linux
Nowadays "RPMForge/!RepoForge - This is a dead project. Not maintained. DO NOT USE.".. this brings me to another topic on converting RPM to DEB packages. Anyway, your life in the Linux or overall *nix world is going to change. You will be like "wtf, I just spent 6 hours trying to install an image editor" and.. that is why Linux is so fucking fun! Because you have to figure shit out. On Windows sure you can click install and life goes on, but you never realize what went into making that happen - probably.
Start learning today, switch to Linux or at least begin running any Linux distribution in VirtualBox or VMware. What are you waiting for in 2020? Fucking do it! Be an Internet ninja with me... us.
Forget MSI and say hello to RPM and DEB - https://unix.stackexchange.com/a/374229 .. sure you type more commands and shit, but once you learn how these commands work, what they do, your life will change for the better - things get done faster and you might see file sizes like 2MB instead of 18MB. Because Linux is beautiful.. and Windows is bloated, full of extra, and in my opinion sometimes and actually most of the time you will find better stability within the Linux world.
With that said, get Debian or Ubuntu inside VirtualBox or VMware.
Now.. let me say that you can just use an ISO file to install your own VM. I actually recommend this most for security reasons. With the osboxes virtual image, you are trusting some random fucker - jk but not really jk.. some person on the Internet installed the iso inside VirtualBox or VMware then took the VM file - then they upped it to SourceForge so you are going from trusting the Debian ISO, to trusting the Debian ISO, the ISO installer man, and trusting SourceForge.. additional risk of 2 parties. Fuck that! Give me the original source - every time.
Debian ISO: https://www.debian.org/distrib/netinst - click amd64 as amd64 = AMD and Intel 64-bit processors we will see 32-bit architecture losing support as we get closer to 2030s but even now 32-bit just sucks ass - so anytime you see "amd64" get excited and do that - every time. If you don't need amd64 then you probably know what you need, I hope!

Ubuntu ISO: https://ubuntu.com/download/server
Then you will take your ISO file of Debian/Ubuntu and load into your VM (virtual machine). Keep in mind that your hypervisor of choice is great at providing virtualization.. but will only take the resources you provide it. You'll want to give your virtual environment plentiful RAM and CPU to work with. I typically go half-half for example if I have 16GB of RAM, I'll give my virtual environment 8GB RAM.
Now let's move onto actually using our VM to begin making a website scanner (firstly we will check port 80 and 443) as these are the most common website ports - HTTP (80) and HTTPS (443). Port 80 is used for unencrypted website traffic, so if you login to a website using http:// and not https:// your password "Horse1" gets sent across the whole fucking hops nodes path as "Horse1" instead of scrambled w/ encryption like "fiaef89wef89w0rt4965654y89t98g98g8959y5"*bits cryption... so yeah, umm HTTPS is pretty fuckin' good - real talk. Port 443 is better than port 80 for security, because encryption keeps information safer while in transit. It's like bulletproof armor walking through a war zone. Turn HTTPS (443) on and let HTTP (80) die. Can you still get sniped in the head with a sniper rifle? Sure, but you are protecting your heart (password) and other vital organs (username and involved systems) from stray bullets like basic MITM/sniffing of traffic.
This brings me to one other point, downloading files over HTTPS (443) is far safer because otherwise it is a possibility someone could more easily provide you an incorrect file. Let's say you go to download an ".exe" file, an attacker on WiFi could perhaps feed you a malicious executable file you then launch on Windows. Wouldn't you see other stuff look wrong though? Someone could proxy the requests through and when you fetch the exe, only then they offer the malicious binary. It may sound complicated and overly complex, but this shit is easy. They pretty much make run-click-fuck attacks nowadays. So use HTTPS.
It's more common to have prepackaged tools for causing damage than in past years, because as security is improving, attacks are being made easier to launch because attacks are getting stronger with ease-of-use in mind. It's a back-and-forth battle between security and anti-security. Many describe this as "cat and mouse".
'ways, here we are.






RAM: 4096
CPU: NUM of proc = 2, NUM of cores = 2
All set: Close, Finish
Power on this virtual machine
---
The instructions for VirtualBox are different, I used VMware so figure VirtualBox yourself or find a VMware key online lol (like maybe the store if you have money or whatever..).
If you are new, continue on using Graphical install. This walks you through installing the Linux system. Mostly just click Continue/Next through.
A point will be reached, you will see "Hostname:" set this to dev.ciphers.pw
If you want...
For the root password set something safe like: Bad#Guess2day
Name for new user: Ciphers
Username: ciphers
Password: Bad#Guess2day
Same user pass as root pass ftw, super secure!
For the disk partitioning:
Guided - use entire disk
Keep clicking Continue/Next until you get to...
Partition disks... "If you continue, the changes..."
SELECT "Yes", Continue
Your Debian system will install...
With the above password, I am certainly assuming you are not setting this up to be Internet accessible via SSH.
In the case you are being a dumb clown (unintentionally) and I have to make this tutorial dumb enough for those newly people, I will do that a little below.
"If you wish to scan another CD"... No, Continue
Keep clicking Continue/Next through the remainder.
When prompted for "popularity-contest", leave No selected and Continue.
Uncheck everything except "Debian desktop environment" and "standard system utilities".
When asked to install the GRUB boot loader, keep Yes and Continue.
Select /dev/sda ... Continue.
You will now be installing the system and almost ready to begin actually making your (probably first ever) port scanner on a Linux system - in C++.
---
We will be using GCC, keep in mind MinGW is a port of GCC over to the Windows OS... anyone wanting to make this on Windows can but I promise making this on Linux is going to be more exciting.
Login to your freshly installed Linux system with your password (or Bad#Guess2day).
Top right click Activities > search Term > Enter
This opens Terminal.
Code:
suWhen prompted "Password:", enter your password (or Bad#Guess2day).
On Linux, the text password characters will not appear as you type. This is intended for obvious security reasons, similar to * showing up in a password field.
GCC is good
Code:
apt install gccWe should also get g++
Code:
apt install g++Type "Y" for yes, Enter, to install gcc.
Code:
sudo apt-get install libsfml-devAlternatively you may install this as mentioned in the SFML tutorial.
We will be referencing two pieces, firstly this https://www.sfml-dev.org/tutorials/2.5/network-socket.php and secondly this old dinosaur of a scanner code http://www.cplusplus.com/articles/o2N36Up4/
Do this
Code:
sudo apt-get build-dep libsfml... okay tbh fuck idk man - just fuck.
Let's just make a text file (CPP) in our home folder:
Code:
cd ~
nano scan.cpp
Code:
#include <iostream>
#include <SFML/Network.hpp>
#include <string>
static bool port_is_open(const std::string & address, int port) {
return (sf::TcpSocket().connect(address, port) == sf::Socket::Done);
}
int main() {
std::cout << "Port 80 : ";
if (port_is_open("localhost", 80))
std::cout << "OPEN" << std::endl;
else
std::cout << "CLOSED" << std::endl;
return 0;
}Save this to your file (Ctrl+X), Y, Enter
Code:
g++ scan.cpp -lsfml-network -lsfml-systemYou will probably have an "a.out" file appear.
Code:
chmod +x a.outNow... install a web server and launch it to start port 80 listening.
Code:
apt install apache2 -yRun your compiled single port checker
Code:
./a.outShutdown your Apache web server:
Code:
systemctl stop apache2We will now see if we run our port 80 checker tool:
Code:
./a.outWe see:
Code:
Port 80 : CLOSEDThis is not super complex or crazy awesome - but this is a VERY basic port scanner at that and you have just been shown how to compile this to be working.
From here, you have the basics to get started with a larger project that can go on to scan more ports, maybe optimize the code and read a hosts list etc.. hope this was fun and simple.
- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
- Thread starter
- #9
How much RAM do you have and can you read some of the information here and let me know what works for you (if something does)?CPU: Ryzen 5 2600
Also if nothing works there, let me know and I will take your log file so we can get this fixed <3
- Jun 9, 2016
- 277
- 111
- 107
Sure, but @Asphyxia don't you think its a little bit better if we use Python instead of C++ since its easy and probably all hacking tools, security tools built using Python.
And by the way, take this advice please stop writing 10K lines, because most of the people won't read it all.
Personally I've read the beginning then I stopped and said "WHAT THE HELL HOW AM I SUPPOSED TO READ ALL OF THIS",
If you want to explain something or make a tutorial about something, just make another thread or a Youtube video, it would be better.
Thank you very much.
And by the way, take this advice please stop writing 10K lines, because most of the people won't read it all.
Personally I've read the beginning then I stopped and said "WHAT THE HELL HOW AM I SUPPOSED TO READ ALL OF THIS",
If you want to explain something or make a tutorial about something, just make another thread or a Youtube video, it would be better.
Thank you very much.
- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
- Thread starter
- #12
Without writing lines, there is no content here. A lot of the material is images and code (bash/C++) - pretty much a picture book.stop writing 10K lines
You are right, most people do not read because most people do not research security nor program a single byte of code - a couple years ago we had a security team writing many crashes for TeamSpeak 3 (client and server). People just want to leech primarily, I have realized this in running a 70,000 user forum. If you can make anything that people "want to take", they come running and begging for... that.most of the people won't read it all
I normally do both, this is all relevant though. If someone wants to join our security team they are going to learn C++ even if that means they only know how to produce an ELF executable using GCC for C and G++ for C++ - they are going to start with learning something about C++ because Python is nice but C++ is DEFINITELY better. Do not just take my word for it, read over here. There is more comparison of C++ and Python here.make another thread or a Youtube video, it would be better.
Just because something is easy does not make that right. Is Nmap written in Python? Nmap was written in C then ported to C++. ZMap was written in C. Masscan was written in C. Are exploits written in Python? Why sure. Python is a "make it quick" language, simple to learn and work with. Again, just because Python is a 1-2-3 language does not mean that the language is better solely because Python is an easy language.if we use Python instead of C++ since its easy
TL;DR go read https://www.hackerfactor.com/blog/index.php?/archives/825-8-Reasons-Python-Sucks.html no free pony. People have to read and do work to make awesome things happen for example CipherSpeak will not write itself and especially not in Python.
Here is that video if you do not like reading detailed forum posts.
One final note: I mentioned this is for EVERYONE (all skill levels). If any of the content is too slow, use your scroll wheel or better yet PGDN? Not trying to be mean at all but the point of a forum is to have meaningful posts with useful content. If I just said "Know C++ port scanner" and had no info on how to compile one, no one would have a chance to learn. Some people learn with a LITTLE help and I try to provide this..
Last edited:
- Jun 9, 2016
- 277
- 111
- 107
First of all u didn't get my point right about the writing thing,
What I did mean is, its a human nature that they won't read something that is not organized and contains a lot of LINES and images
So basically, what I meant is instead of putting all things together, you could do something like this:
A Separate thread "How to install Your Security VM" for an example,
A Separate thread "Your first step with Port scanning" also for an example,
And then when you write you could link the THREADS,
That's not gonna help me or any one reading only,
its also gonna help Ciphers website imagine someone searching in the internet "How to install Security VM" for an example, they would find Ciphers website of course its not gonna be that easy but its just some SEO things you have to do and backlinks in order to be in the first positions in Google Search.
--------------------------------------------------------------------------------------
About the python thing,
I completely agree with you that C and C++ is the best, but as I clearly see your doing beginner tutorials Probably (Your way into Security),
So as any beginner, it would be easy for him to learn Python and practice with it.
We all know that Python is much more beginner-friendly, while C++ is a more complicated, low-level language.
Personally I would definitely learn C++ as I do have programming experties but beginners I don't think they will succeed easily.
@Asphyxia, if you are gonna help & teach beginners always ask your self, Will it be easy for a beginner? or remember when you was a beginner and ask your self.
Thank you very much.
What I did mean is, its a human nature that they won't read something that is not organized and contains a lot of LINES and images
So basically, what I meant is instead of putting all things together, you could do something like this:
A Separate thread "How to install Your Security VM" for an example,
A Separate thread "Your first step with Port scanning" also for an example,
And then when you write you could link the THREADS,
That's not gonna help me or any one reading only,
its also gonna help Ciphers website imagine someone searching in the internet "How to install Security VM" for an example, they would find Ciphers website of course its not gonna be that easy but its just some SEO things you have to do and backlinks in order to be in the first positions in Google Search.
--------------------------------------------------------------------------------------
About the python thing,
I completely agree with you that C and C++ is the best, but as I clearly see your doing beginner tutorials Probably (Your way into Security),
So as any beginner, it would be easy for him to learn Python and practice with it.
We all know that Python is much more beginner-friendly, while C++ is a more complicated, low-level language.
Personally I would definitely learn C++ as I do have programming experties but beginners I don't think they will succeed easily.
@Asphyxia, if you are gonna help & teach beginners always ask your self, Will it be easy for a beginner? or remember when you was a beginner and ask your self.
Thank you very much.
- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
- Thread starter
- #14
SEO is not really going to help us, we switched from r4p3.net to ciphers.pw to meet the wants of some people that r4p3 did not sound good (unprofessional). We did this domain transitioning during a time where TeamSpeak was dying (more accurately, hanging by a thread).its just some SEO things you have to do and backlinks in order to be in the first positions in Google Search.
This speaks for itself:
TeamSpeak is a joke and totally destroyed. R4P3 (former name of us/forum/security-team-members)... found many security vulnerabilities in the TeamSpeak project and that is honestly the only reason this forum started.
TeamSpeak is dead; RIP.
I appreciate your positive suggestions but there is not a tremendous amount of activity here primarily due to lacking a strong security team.
You can't solo security research and development (R&D). It is time consuming, requires exhaustive man hours searching different things, performing many different types of security tests.
We used to have 6 people all finding security holes in a single platform - that was fun. That is what delivers quality content. Shy of a security team, there is simply not much to deliver. I was only asking for people to show some interest in learning C++ here
If you think Python should be the language, feel free to start a Python security team here.
Last edited: